
Spring Semester, 1999
Heuristics 3
© 1999, All Rights Reserved, SDSU & Roger Whitney
San Diego State University -- This page last updated 21-Mar-99

|
CS 535 Object-Oriented Programming & Design Spring Semester, 1999 Heuristics 3 |
|
|---|---|---|
|
© 1999, All Rights Reserved, SDSU & Roger Whitney San Diego State University -- This page last updated 21-Mar-99 |
Keep it Small
2.3 Minimize the number of messages in the protocol of a class
2.5 Do not put implementation details such as common-code private functions into the public interface of a class.
2.6 Do not clutter the public interface of a class with things that users of the class are not able to use or are not interested in using.
3.7 Eliminate irrelevant classes from your design.
3.8 Eliminate classes that are outside the system.
Common Minimal Public Interface
2.4 Implement a minimal public interface that all classes understand
This can be applied a global Object class, but also applies to classes in a project or domain
Java’s Object clone()
|
notify() |
wait(long
timeout)
|
|
notifyAll() |
wait(long
timeout, int nanos)
|
|
wait() |
|
Operations, Classes, Methods
3.9 Do not turn an operation into a class
Does it make sense to have:
Relationships between Objects
Type of Relations:
|
Type |
Relation
between
|
|
Uses |
(Object) |
|
Containment |
(Object) |
|
Inheritance |
(Class) |
|
Association |
(Object) |
Six different Ways to Implement Uses
How does the sender access the receiver ?
1. Containment
class Sender {
Receiver here;
public void method() {
here.sendAMessage();
}
}
class Sender {
public void method(Receiver here) {
here.sendAMessage();
}
}
3.
Ask
someone else
class Sender {
public void method() {
Receiver here = someoneElse.getReceiver();
here.sendAMessage();
}
}
class Sender {
public void method() {
Receiver here = new Receiver();
here.sendAMessage();
}
}
Singleton
Intent
Insure a class only has one instance, and provide a global point of access to it
Motivation
There are times when a class can only have one instance
Applicability
Use the Singleton pattern when
Examples of Singleton Usage
Java Security manager
Implementation
Java
// Only one object of this class can be created class Singleton { private static Singleton _instance = new Singleton(); private Singleton() { fill in the blank } public static Singleton getInstance() { return _instance; } public void otherOperations() { blank; } } class Program { public void aMethod() { X = Singleton.getInstance(); } }
Note: Java does garbage collection of classes. It is possible that the class Singleton can be garbage collected. The class will be garbage collected only if there are no references to the class or any references to any instances of the object in the JVM. If the singleton class is garbage collected, the next time Singleton is referenced, a new instance of the Singleton class will be created. If the Singleton object changes state over time, this can be a problem. It is possible to turn garbage collection off. (This is done using the -Xnoclassgc flag to java.). If this is not possible, you will need to insure there is always a reference to the class or an instance of the class.
Implementation
C++
// Only one object of this class can be created class Singleton { private: static Singleton* _instance; void otherOperations(); protected: Singleton(); public: static Singleton* getInstance(); }Implementation File Singleton* Singleton::_instance = 0; Singleton* Singleton::getInstance() { if ( _instance == 0 ) _instance = new Singleton; return _instance; }
Heuristics for the Uses Relationship
4.1 Minimize the number of classes with another class collaborates
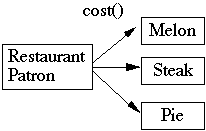
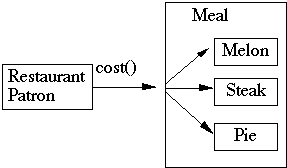
4.2 Minimize the number of messages sends between a class and its collaborator
4.3 Minimize the number of different messages a class sends to another class.
4.4 Minimize the product of the number of methods in a class and the number of different messages they send.
Which is more complex?
Containment Relationship
4.5 If class A contains objects of class B, then A should be sending messages to its fields of type B.
This heuristic prohibits:
class Foo {
Bar data;
public Bar getData() {
return data;
}
public void setData( Bar newData) {
data = newData;
}
}
Narrow and Deep Containment Hierarchies
Combining fields into new classes can reduce the number of fields in a class
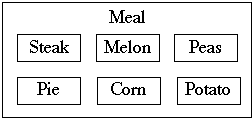
A broad and shallow Containment Hierarchy
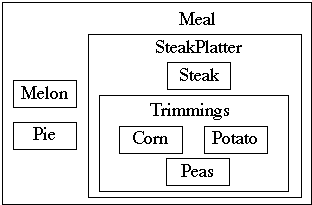
A narrow and deep Containment Hierarchy
4.8 Distribute system intelligence vertically down narrow and deep containment hierarchies.
No Talking between Fields
4.14 Objects that are contained in the same containing class should not have a uses relationships between them.
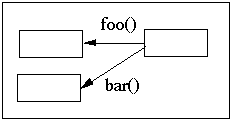
Contained Objects with uses relationships
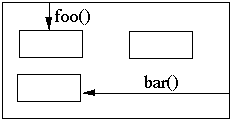
The containing class should send messages to the contained objects
4.13 A class must know what it contains, but it should not know who contains it.
If a number of classes depend on each other in a complex way, you can violate 4.13 to reduce the number of classes they interact with.
Wrap the classes in a containing class.
Each contained class sends a message to the containing class, which broadcasts the message to the proper contained objects
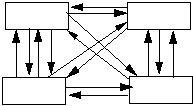
Complex interactions
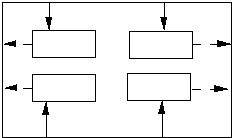
Replacing complex interaction with containing class
Copyright © 1999 SDSU & Roger Whitney, 5500 Campanile Drive, San Diego, CA 92182-7700 USA.
All rights reserved.
Previous visitors since 04-Mar-99 Next